The Essential Eight (E8) is a framework maintained by the Australian Signals Directorate (ASD), and it provides a great path towards an enhanced Cyber Security Posture. The ACSC have determined the top eight attack vectors (and related mitigation strategies) used in the vast majority of compromises.
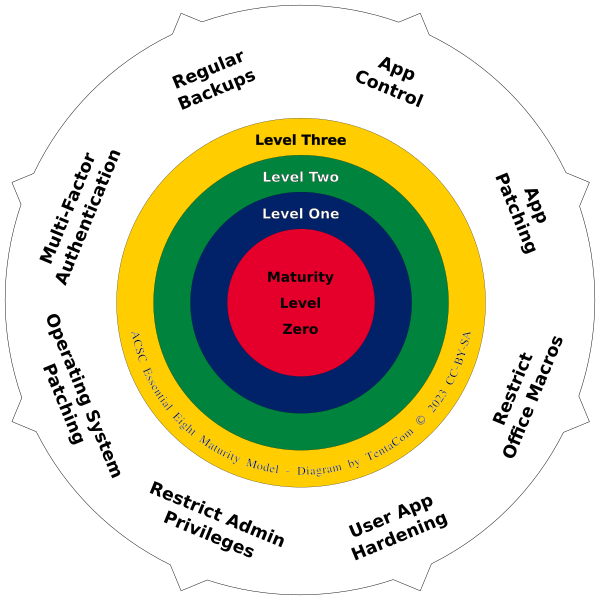
All of the E8 are important, thus we depict them in a circular diagram:
Approach
Contrary to most other other Information Security frameworks, E8 does focus on actual implementation, so it explicitly does not take a risk-based approach. (Don’t believe anyone who tells you that it is risk-based.) How a particular control is implemented could be a risk-informed choice, but the objective of the control must be achieved. Implementing a control is not optional. Australian Federal and State Government entities have specific requirements on which maturity level they must aim for, as do defence contractors and some other government contractors.
Additionally, we must always keep in mind that “the baddies don’t care”. Either opportunistic or targeted, your organisation can have a cyber security incident. An opportunistic burglar goes from house to house along a street to check out whether doors and windows are locked, and the house with less security has a higher chance of being targeted. Online, malicious actors do pretty much the same, from anywhere in the world, and they have automated tools to do most of the reconnaissance work!
Not everything can be automated though, and malicious actors also have limited resources. So if your organisation has, for instance, Multi-Factor Authentication (MFA) active for all staff, you have a much lower chance of becoming a victim. The ASD research and data over the years has clearly shown this, which is why MFA is in the E8. MFA is not perfect, but having it is much better than not having it. And there are more security forms of MFA, too.
E8 Maturity Levels
In addition to the eight Mitigation Strategies, there are three Maturity Levels (ML1 to ML3, three being the highest maturity level). Australian Federal and State Government entities have specific requirements on which maturity level they must aim for, as do defence contractors and some other government contractors. It is important to start with an ML1 assessment (see this also as a gap analysis), followed by a remedial implementation phase, before addressing ML2. Most organisations do not need to implement ML3.
Assessment (Audit)
As we have Certified Essential Eight Assessors, TentaCom can assess the controls at a particular Maturity Level for each of the Mitigation Strategies within your organisation, and provide you with an official assessment report. An E8 assessment is a serious understaking, and for a larger organisation or government entity can take take considerable time. For an SMB that is not required to implement the E8 but wishes to security posture efficiently (an excellent idea!), various variations are possible.
After initial scoping, an E8 assessment is a very practical endeavour where for instance specific policy settings within your environment are verified. By scopying we mean reviewing what your environment looks like, how many different types of systems (desktops, servers, operating systems, etc) you have. An E8 assessment almost always covers your entire organisation.
Please note that as per the ASD E8 assessment guidelines, the ML of each mitigation strategy is the ML of the lowest rating control within that mitigation strategy. For assessment purposes, there is also a Maturity Level Zero, indicating that no control or mitigation strategy has as yet been applied, or the applied controls are ineffective. The overall ML of the organisation is the lowest ML of all mitigation strategies. You cannot leave out mitigation strategies from an assessment (they would be rated ML0 anyway).
Assessment Report
Many tenders and contracts at any level of government, as well as insurance providers, now often ask for either an Assessment Report aligned with a recognised framework (such as E8, ISO 27001, or NIST), or ask questions that are directly aligned with one of the frameworks. Therefore, getting on this early wil put you in good stead, and actually save a lot of time and effort. The E8 is a good starting point.
Showing a solid third party report carries extra weight. We can work with any of the abovementioned frameworks, and more. But we’ll mention it again: E8 is an excellent one to start with; while looking more achievable, it can be very meaningful.
More on Insurance
We have noticed that insurance providers now often either won’t insure if you haven’t started working on your Security Posture yet, or they might rate your unknown risk as much higher, with accompanying premiums. In addition, we have seen insurers actually reporting back to clients with results from proactive vulnerability scans of the public-facing infrastructure of their organisation! So that’s really interesting, seeing insurers now taking such an active interest in their clients’ Cyber Security Posture. The bar is being raised, and that’s appropriate for the rapidly evolving global threat environment!
TentaCom E8 Services
In addition to the E8 Maturity Assessment and Report, of course we include recommendations and suggested priorities in our report. You can run with that internally, or, if you like, have us assist you with the effective implementation of these recommendations, enhancing your Security Posture.
Eager to start your guided Essential Eight journey, or have more questions? Contact us today!